Long before computers and smartphones were the norm, encryption emerged as a method of hiding messages from prying eyes. The origins of encryption can be traced back to early civilizations, where ancient cultures hid their secret messages and mysteries behind enigmatic signs and symbols.
In classical antiquity, the Egyptians used hieroglyphics, a complex system of symbols and images, to veil their communications. And the Greeks invented the Scytale, a cylindrical stick on which text was written and then unrolled to reveal a legible message. These were the fledgling attempts to protect information from unauthorized viewing.

The Caesar cipher Deciphered
It was Julius Caesar, the powerful Roman ruler, who would lend his name to one of the earliest and simplest forms of encryption. Caesar coding, known by several names including Caesar rotation, or Rot for short.
Julius Caesar used this secret writing to communicate with his field commanders. In the case of Caesar coding, the method was very simple: all you had to do was move each letter in your message forward or backward by a certain number of positions. This number is called the key. You shared the key with the recipient of your message so that only they could decipher your message.
Let’s see how this would work in practice. Imagine Caesar wants to send the following message to his troops, “ATTACK.”
First, he (the sender) and his troops (receiver) would have to agree on a key. They should do this personally before going to war. Let’s say they agreed on the key 3.
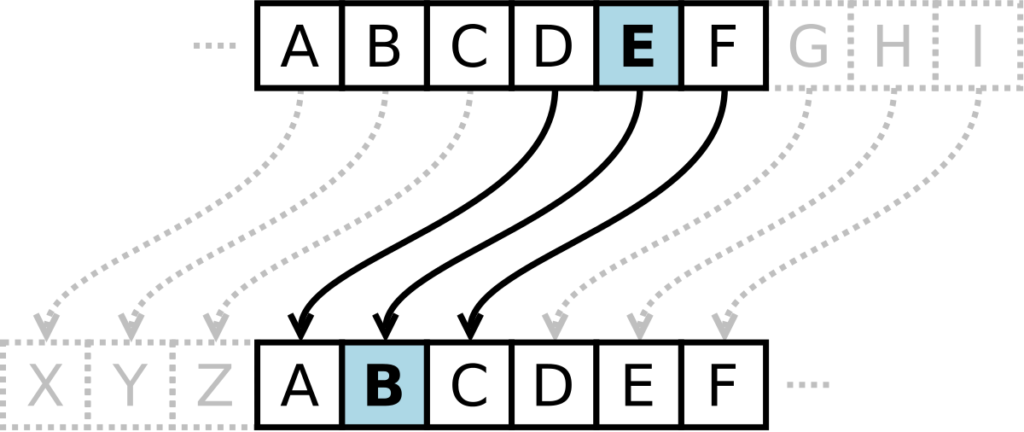
To encrypt his message, Caesar would shift each letter forward by 3:
Then he would openly send this message to his troops. Any enemy troop that intercepted the message would not know what it meant. Even if they knew the Caesar encryption operation (shifting letters forward), they still could not decrypt it because they did not have the key (3). Cryptographic algorithms are operations that are publicly known but are still unbreakable because the key used in each case is kept secret.
After Caesar’s troops received his message, they were able to decode it by shifting each letter back 3 places:
Pretty simple, right? Now imagine you were part of the enemy troop and charged with cracking Caesar’s code. How would you go about that? Are there any weaknesses or flaws in this code that stand out to you?
It took mathematicians 800 years to crack the Caesar cipher. They finally cracked the code by looking at a key feature of language. In any language, some letters are used more often than others. In fact, in any book you can count how many times each letter appears and you will notice the same pattern.
In the Renaissance, Vigenère coding emerged, which used a more complex approach. This involved using a key word to shift letters in the message. The resulting secret code was much more difficult to crack, but eventually clever minds had managed to unravel even this method.
The Enigma Machine
During the dark days of World War II, the infamous Enigma machine revolutionized the world of encryption. This complex machine created seemingly unfathomable mysteries through rotating wheels and cable connections. Cracking the Enigma code became an obsession for Allied cryptanalysts, and their eventual success had a significant impact on the course of the war.

How it worked: Imagine you wanted to code a message. You would then set up the Enigma machine according to the daily key, and for each letter you wanted to encrypt, you pressed a key on the keyboard. At that point, the machine would reveal a new letter on a lamp sign, which represented the coded letter. The recipient would have an Enigma machine set up the same way and could decipher the encrypted text by pressing the corresponding key on his machine.
The biggest mystery for the Allies was not only the mechanism of the Enigma machine, but the daily changing of the key by the Germans. Each day the machine was set according to a new key, and the only way to decipher the messages was to find the correct key for that day.
To break this code, the Allies had to employ some of the smartest minds in the world. Alan Turing, one of the most famous mathematicians and computer pioneers of all time, led a team of codebreakers at Bletchley Park in England to crack the Enigma codes. They used sophisticated methods and early computers to sift through the trillions of possible key combinations. This was filmed in the movie The imitation game. Highly recommended!
The Allies’ ultimate success in deciphering the Enigma codes had a huge impact on the course of World War II. They were able to intercept secret German communications and obtain strategic information. This highlight in the history of cryptography showed how the art of encryption and decryption, even in the face of a technological challenge like the Enigma machine, could influence the course of history. It also indicates that any form of encryption is breakable. Also the modern forms.
Symmetric and Asymmetric Encryption
In the world of digital security, there are two main ways to protect data: symmetric and asymmetric encryption.
Symmetric encryption uses a single key to lock and unlock data. It’s like having a special password to protect your data. It works well, but you have to make sure you keep that password safe. An example of a symmetric encryption algorithm is the Advanced Encryption Standard (AES). AES is widely used to encrypt data, such as files, emails and sensitive information. It uses the same key for both encryption and decryption.
Asymmetric encryption is like a pair of keys: a public and a private key. Anyone can encrypt your data with the public key, but only you, with your private key, can make it readable again.
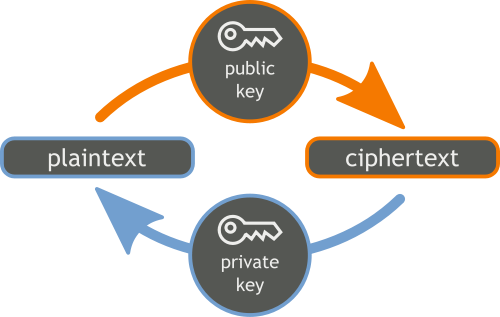
An example of asymmetric encryption
Imagine Alice wants to send a secret message to Bob. Bob could just pin his public key to the supermarket bulletin board, so to speak, for anyone to use to send him encrypted messages.
- Alice knows Bob’s public key (which is therefore accessible to everyone).
- She uses this public key to encrypt her message before sending it.
- Once Bob receives the encrypted message, he uses his private key to decrypt it and read the original message.
This process allows you to securely transmit data over public networks without worrying about prying eyes. Even if someone intercepts the encrypted message, it cannot be decrypted without Bob’s private key.
An example of an asymmetric encryption algorithm is RSA (Rivest-Shamir-Adleman). RSA uses a pair of keys: a public key to encrypt data and a private key to decrypt it. It is often used for secure communications, digital signatures and online security.
Quantum Computers and the Future of Encryption
The emergence of quantum computers has turned the world of encryption upside down and poses a new challenge to the security of digital communications. Quantum computers may crack current cryptographic methods in the future due to their ability to perform massive amounts of computation at lightning speed. This means that many of the methods considered safe today could become vulnerable in a world with powerful quantum computers.
Squatting retroactively
Currently, huge amounts of sensitive data are stored securely with the best security methods available. But, there is a future risk: quantum computers. These powerful machines are capable of cracking current encryption methods. This means that sensitive information now considered secure, such as personal data and trade secrets, can now be intercepted and stored by malicious parties with the intention of deciphering it later once quantum computers are sufficiently advanced.
This has huge implications for the privacy and security we now rely on. This could have major implications for people, businesses and even national security.
So we need to start thinking now about how we are going to protect ourselves from this danger.
How can you protect against the threat of quantum computers?
You can, of course, consider no longer storing your sensitive data in the cloud. But that, of course, is not feasible for many organizations.
Symmetric encryption
It has been known for years that most common asymmetric cryptography cannot withstand the brute-force computing power of a quantum computer. For example, RSA and the commonly used elliptic curves in HTTPS are susceptible to this.
With symmetric encryption (such as AES), your data is less susceptible to attack by a quantum computer. With a powerful algorithm such as AES, symmetric encryption with a key length of 256 bits offers sufficient cryptographic resistance to a quantum computer (for now). So you can increase the length of existing symmetric keys to 256 bits.
Post-Quantum Cryptography (PQC).
Post-Quantum Cryptography (PQC) is a cryptographic approach based on mathematical problems that are quite challenging even for quantum computers. Work is actively underway to develop new PQC standards, which could replace the current asymmetric standards in the future.
In conclusion
Finally, it is important to remember that at a time when concerns are growing about the vulnerability of our data to quantum computers, it is wise to take extra steps to secure your privacy.
One of the handy tools for this is VeraCrypt, which allows you to robustly encrypt your sensitive data. VeraCrypt is a free open source encryption software for Windows, Mac OSX and Linux.
To encrypt just a folder or file, you could also use 7zip (windows) or Keka (mac). As long as you encrypt the file with AES (256).
While experts are working on quantum-proof solutions, using these tools now can give you additional protection against potential threats from quantum computers in the future.


